Comprehensive Guide to Firewalls: Types, Features, Pros & Cons
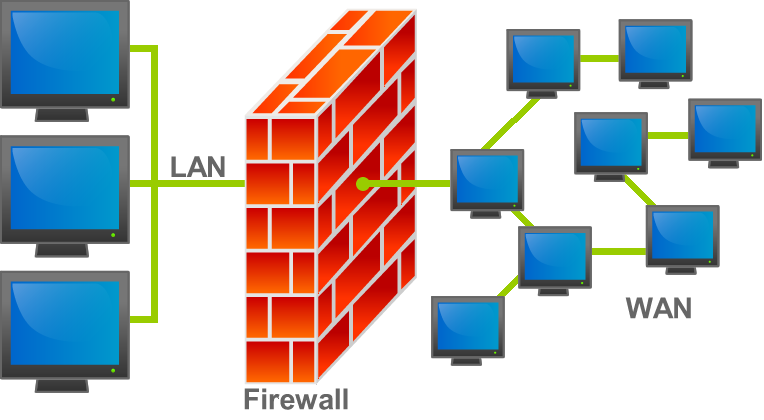
Types of Firewalls: Types, Features, Pros & Cons, and Major Brands Firewalls are the backbone of network security, serving as the first line of defense against cyber threats. Whether you're securing an enterprise or a small business, understanding the different types of firewalls, their features, and the companies providing them is essential for making the right decision. In this comprehensive article, we’ll explore: -- Types of Firewalls -- Key Features -- Pros and Cons -- Top Firewall Providers and Model What is a Firewall? A firewall is a network security system that monitors and controls incoming and outgoing traffic based…